A company purchased and installed a wi-fi, 6 port router (a Chinese made JHC device) in their network. Within several minutes Phen, paired with NeTERS, saw and identified some very strange behavior. There was a new system and it was delivering data at 20k/min rates to and 7k/min from a location in China.
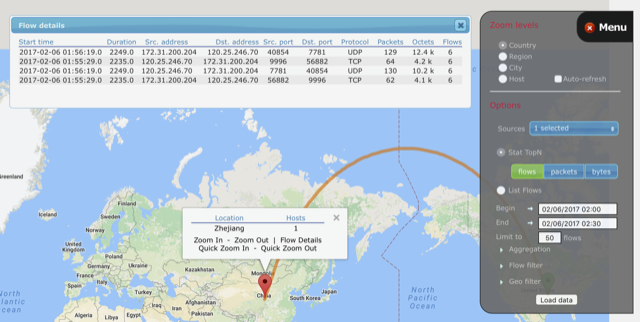
Phen also observed that the data was encrypted UDP traffic going to port 7781. Phen investigated and researched, no data going the wi-fi/router that matched that going to China.
Phen kept observing and the strange behavior continued, somewhere between 15-20 minutes after the wifi/router was plugged in, Phen started taking action.
from 7871 (UDP), 443 (TCP), 8000 (TCP)
/sbin/iptables -I FORWARD -i eth0 -d 120.25.246.70 -p udp -j DROP
from 7871 (UDP), 443 (TCP), 8000 (TCP)
/sbin/iptables -I FORWARD -i eth0 -d 220.243.196.76 -p udp -j DROP
from 7871 (UDP), 443 (TCP), 8000 (TCP)
/sbin/iptables -I INPUT -i eth0 -s 112.124.0.188 -p udp -j DROP
00:41:51.264454 IP (tos 0x0, ttl 128, id 0, offset 0, flags [DF], proto UDP (17), length 84) 172.31.200.204.40854 > 120.25.246.70.7781: [udp sum ok] UDP, length 560×0000: 4500 0054 0000 4000 8011 174d ac1f c8cc E..T..@….M….
0x0010: 7819 f646 9f96 1e65 0040 b1b5 0081 0000 x..F…e.@……0x0020: 0000 0000 0000 0000 ac1f c8cc 9f96 0000 …………….0x0030: 0e6e 2080 a843 0000 7010 1fc5 c749 0000 .n…C..p….I..0x0040: 7d6f c79f 240c 0000 0000 0000 0000 0000 }o..$………..0x0050: 0000 0000
00:41:56.248340 IP (tos 0x0, ttl 128, id 0, offset 0, flags [DF], proto UDP (17), length 80)172.31.200.204.40854 > 120.25.246.70.7781: [udp sum ok] UDP, length 520×0000: 4500 0050 0000 4000 8011 1751 ac1f c8cc E..P..@….Q….0x0010: 7819 f646 9f96 1e65 003c a5b6 0080 0000 x..F…e.<……0x0020: 47a3 1139 9f96 0000 0005 0300 0f76 20fe G..9………v..
0x0030: 0000 1bd4 0000 7037 0000 0000 0000 0000 ……p7……..
0x0040: 0000 0000 0000 0000 0000 0000 0000 0000 …………….
00:42:05.429014 IP (tos 0x0, ttl 128, id 41197, offset 0, flags [DF], proto TCP (6), length 52)
172.31.200.204.56882 > 120.25.246.70.9996: Flags [.], cksum 0x2834 (correct), seq 1182678521, ack 189335902, win 457, options [nop,nop,TS val 53822736 ecr 1600529259], length 00×0000: 4500 0034 a0ed 4000 8006 768a ac1f c8cc E..4..@…v…..0x0010: 7819 f646 de32 270c 467e 3df9 0b49 095e x..F.2′.F~=..I.^
0x0020: 8010 01c9 2834 0000 0101 080a 0335 4510 ….(4…….5E.0x0030: 5f66 236b _f#k 00:42:20.494925 IP (tos 0x0, ttl 128, id 0, offset 0, flags [DF], proto UDP (17), length 84)
172.31.200.204.40854 > 120.25.246.70.7781: [udp sum ok] UDP, length 56
0x0000: 4500 0054 0000 4000 8011 174d ac1f c8cc E..T..@….M….
0x0010: 7819 f646 9f96 1e65 0040 b1b5 0081 0000 x..F…e.@……
0x0020: 0000 0000 0000 0000 ac1f c8cc 9f96 0000 …………….
0x0030: 0e6e 2080 a843 0000 7010 1fc5 c749 0000 .n…C..p….I..
0x0040: 7d6f c79f 240c 0000 0000 0000 0000 0000 }o..$………..0x0050: 0000 0000
Phen started taking action.
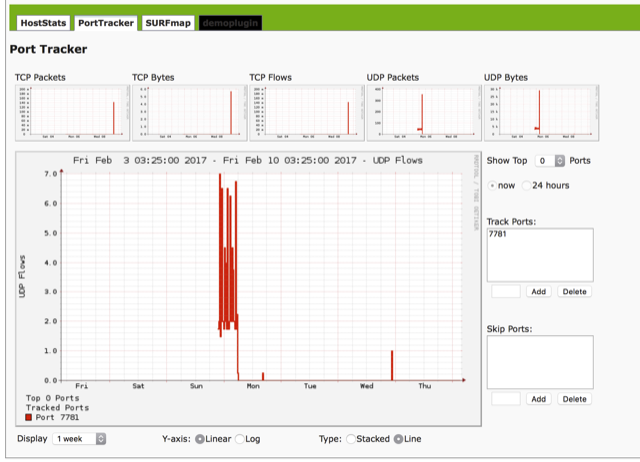
By halting and blocking outbound traffic to the strange networks and port (120.25.246.70 @port 7781)
Since this has been blocked, Phen has observed and monitored data flowing from port 7781 to port 443 and port 8000 using TCP (this is normal encrypted network traffic). With Phen ‘s understanding of how network communications operate and the experience of history that he alone has, Phen came to the realization that this was the same poor traffic of data exfiltration and blocked the two new ports
The traffic then flows (still on the encrypted network platform 443 / TCP, 8000 / TCP) to two separate networks in China. 220.243.196.76 and 112.124.0.188 respectively. At this point, Phen lowered all outbound traffic to and from the hosting company network to China. Since there is no reason for the organization to have any contact with China.
/sbin/iptables -I FORWARD -i eth0 -d 120.25.246.70 -p udp -j DROP
from 7781 (UDP), 443 (TCP), 8000 (TCP)
from 7781 (UDP), 443 (TCP), 8000 (TCP)
/sbin/iptables -I FORWARD -i eth0 -d 220.243.196.76 -p udp -j DROP
from 7781 (UDP), 443 (TCP), 8000 (TCP)
/sbin/iptables -I INPUT -i eth0 -s 112.124.0.188 -p udp -j DROP
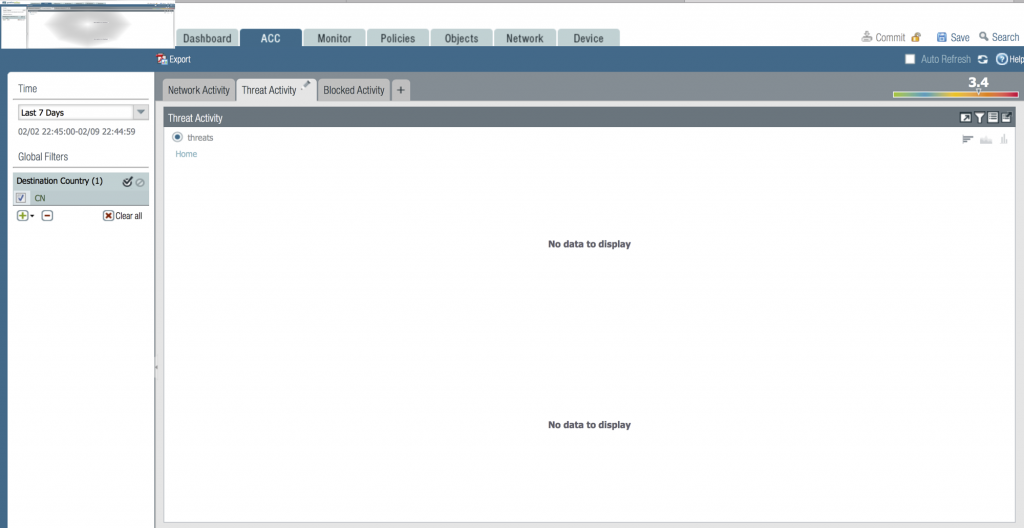
It is worth remembering that the organization had a Palo-alto w / Wildfire mounted that did not alert any irregular or suspicious traffic.
….







