Providing cost affordable CMMC coverage
CMMC-AB marketplace listing “Canfield CyberDefense Group” has been approved.
To view this listing, go to: https://cmmcab.org/marketplace/canfield-consulting-group/

CMMC-AB marketplace listing “Canfield CyberDefense Group” has been approved.
To view this listing, go to: https://cmmcab.org/marketplace/canfield-consulting-group/
CCG’s Artificial Intelligent solutions, CheckMate, is designed to meet, benefit, greatly simplify, and provide an economical cost reduction in the implementation of CMMC Certification pre-assessment and meet compliance requirements.
DoD contractors will need to be certified at the appropriate CMMC level in order to bid on Request For Proposal (RFPs).

Discover the CMMC Level Requirements:
CheckMate is providing direct requirement coverage through level 5:
CheckMate also provides proof of compliance in a Real-Time Continuous Monitoring presentation that is otherwise expected to take 300-600 man-hours for existing networks at Level 2 greatly reducing the cost and simplifying the certification process.
CMMC is the U.S. Department of Defense’s new Cybersecurity Maturity Model Certification. It is a requirement that all contractors and suppliers, primes and subs, establish protocols to protect Controlled Unclassified Information (CUI), Federal Contract Information (FCI), and other data, network, and systems of the Defense Industrial Base (DIB) sector. Previously, companies could self-certify compliance with the appropriate Defense Federal Acquisition Regulations (DFARs). Now companies must pass an audit conducted by a certified third-party assessment organization (C3PAO).
No company will find these activities and their associated costs trivial. Many SMBs possess minimal cybersecurity infrastructure or knowledge, which makes even CMMC Level 1 a challenge. Companies that handle CUI who already must meet DFARS clause 252.204-7012 also face a significant cost hurdle, even though CMMC Level 2 incorporates the 110 security controls of NIST 800-171, for two reasons:
Lower cost to reach and meet compliance through CheckMate w/ Phen, as low as $550/month to provide compliance coverage. Also, providing tools to help provide “proof of coverage” with real-time continuous monitoring solution (CheckMate) to reduce the yearly reoccurring cost of up to $40,000.
The initial cost of cybersecurity compliance is high. Just writing policies and gathering proof of compliance will take 300-600 hours for existing networks at Level 2. Depending on the complexity of your network, engineering, testing, and applying secure configurations will take much longer. Bringing existing systems up to the required level of security can easily take 1,000 – 2,000 consultant hours.
For example, it could take 100 hours for your Linux administrator to fully secure a single Red Hat database server. Then repeat for your web server, your file server, your directory services, your desktops, your backup solutions…
Every time you add a new type of system, you need to review your CMMC requirements against it. For example, even if you secure your database server fully if your file server has a weak password policy, you have a problem.
Consider the implications of failing to attain CMMC certification beyond the requirements set by the Department of Defense and the impact it can have on the fundamental operations of your business. CMMC serves as a means of risk reduction and the risk in question is that of your own organization. The unauthorized release of Controlled Unclassified Information (CUI) leads to an annual financial loss of $600 billion. Who is responsible for the development of stolen intellectual property (IP) and who bears the consequences of lost revenue from compromised IP? The answer is you. Regardless of any mandate by the DoD, why not take measures to safeguard your organization’s IP and why wait for the Department of Defense to instruct you to do so?
If the significance of this information is not convincing enough, then keep in mind that by 2026, every procurement request issued by the Department of Defense will include CMMC requirements. Companies that do not possess the appropriate level of CMMC accreditation as specified in the procurement request will be unable to participate in the contract and will miss out on potential revenue opportunities, even if they are lower-tier members of the winning bid team. These businesses may also find themselves on the sidelines before the full implementation of CMMC as prime contractors and other upstream partners choose to collaborate with companies that have demonstrated a commitment to reducing cybersecurity risks through proactive investment in CMMC. Can your business afford this outcome?
Businesses that comprehend and take a holistic view of, the true cost of CMMC can make appropriate arrangements, safeguard their assets, and attain a competitive edge that will benefit them in the long term.
In September 2020, the DoD published an interim rule to the DFARS in the Federal Register (DFARS Case 2019-D041), which implemented the DoD’s initial vision for the CMMC program (“CMMC 1.0”) and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
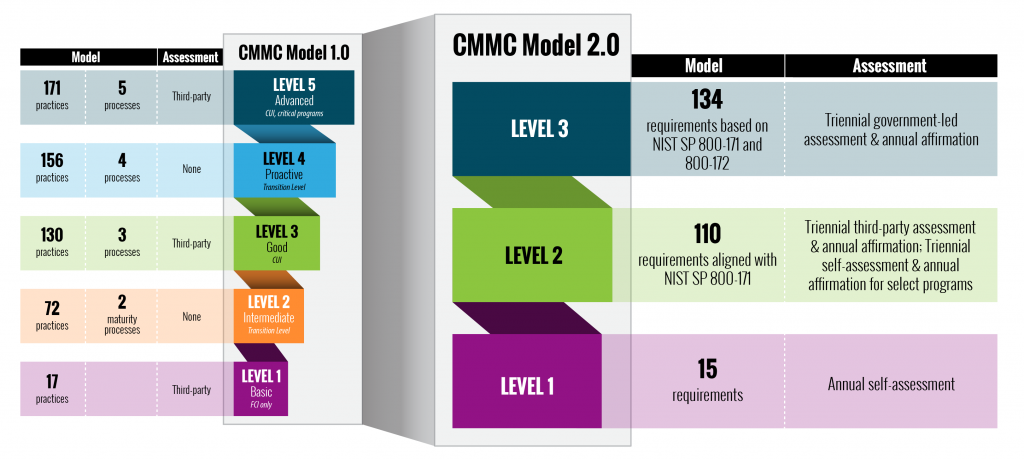
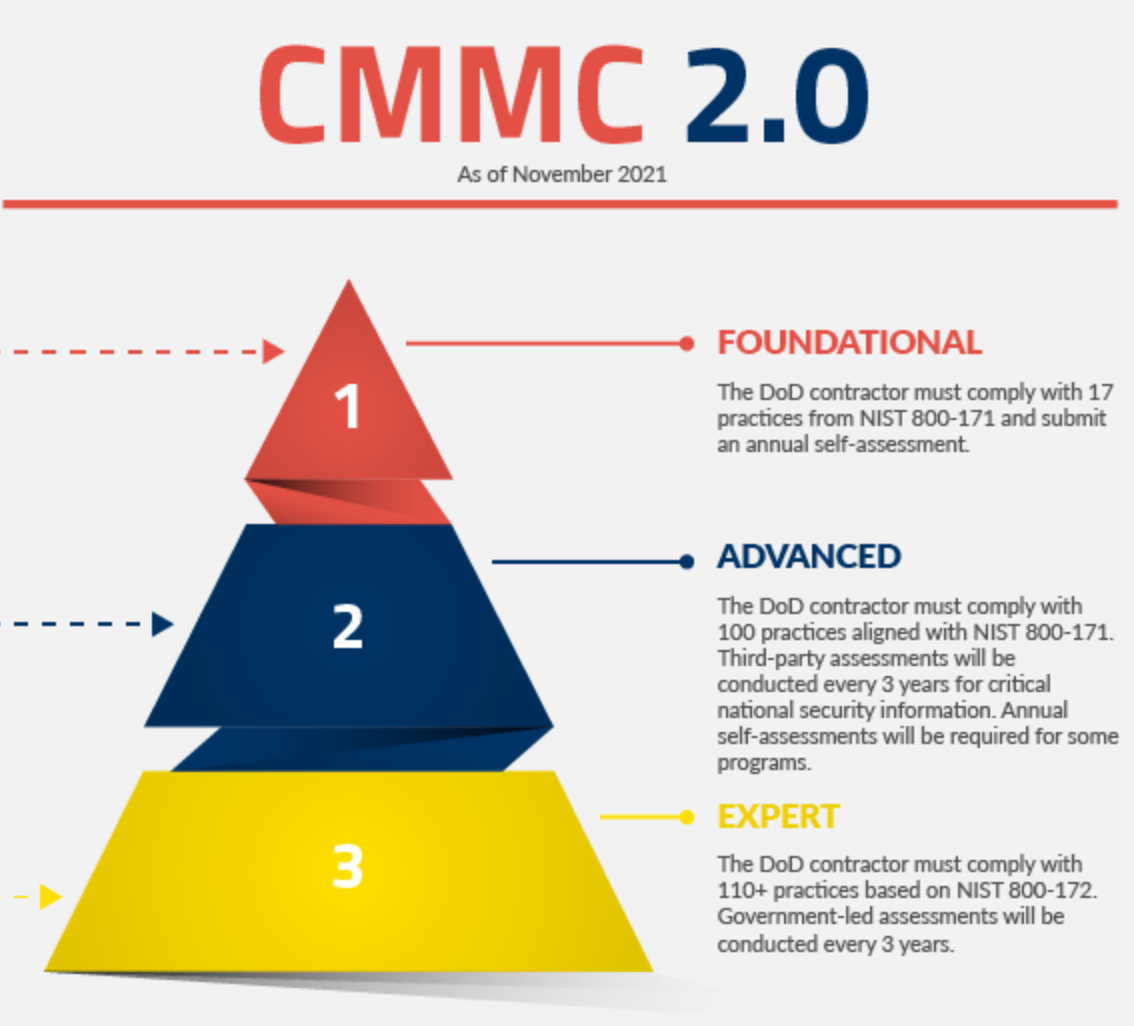
The CMMC framework consists of five maturity levels – Level 1 through 3 –