As more devices come online, indiscriminate cybersecurity threats are increasing. Any entity operating in the digital domain is vulnerable. The average time from accessing the internet to being scanned by a threat actor is seven minutes. 70% of attacks originate from inside the network. Firewalls are not the solution for insider threats. That is why our customers are reaching out to CCG for Phen; our cognitive learning Artificial Intelligent and Matching learning technology with deep packet inspection to support in the detection and protection of cyber threats at an unprecedented speed with minimal to no human involvement.
PHEN.AI
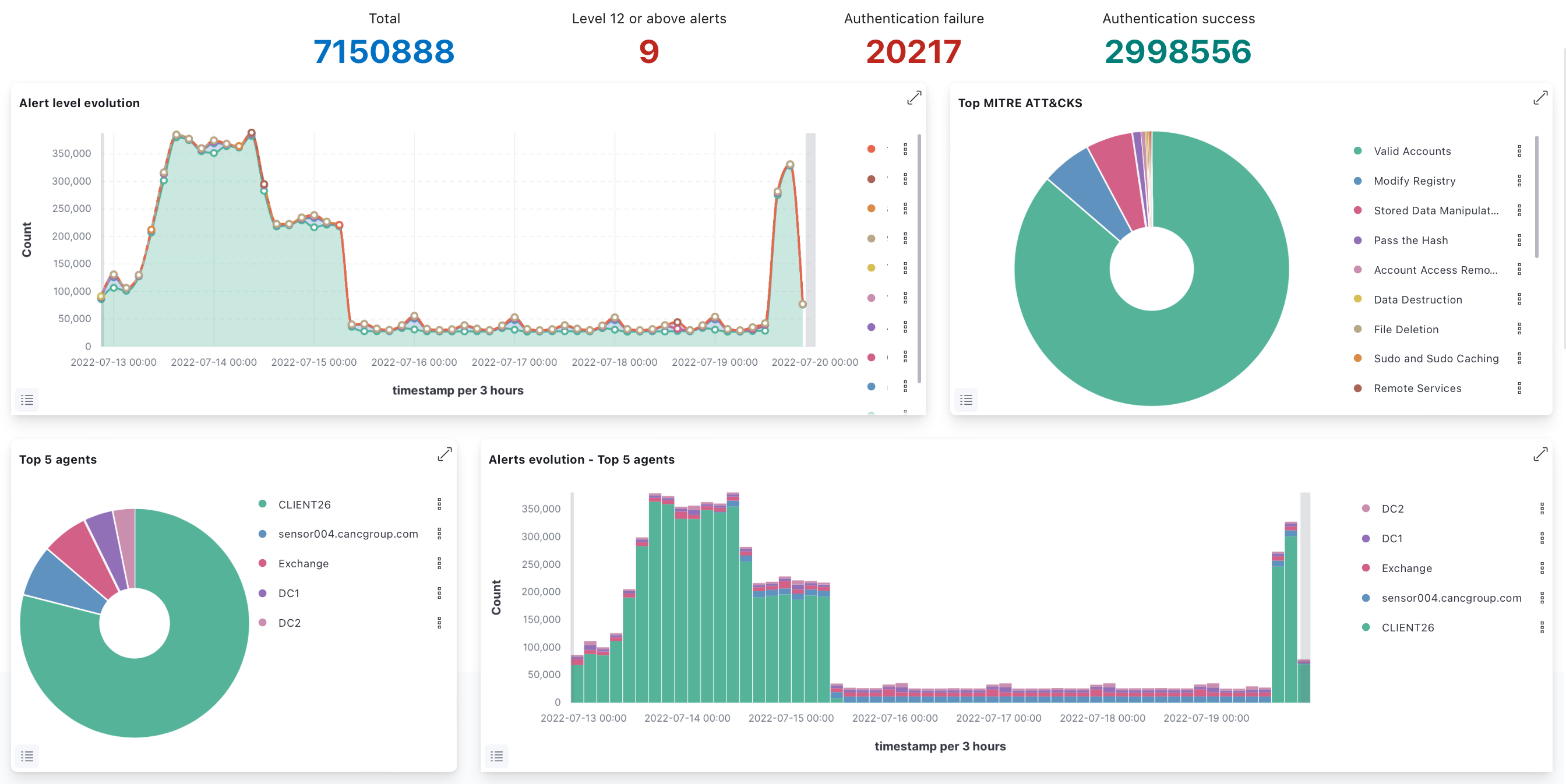
Phen.AI CCG’s proprietary cognitive learning Artificial Intelligent, patent-pending has been designed with methods to independently analyze systems, hunt for insider threats, and score these threats in order to help establish which systems are critical and recommend what additional protections are required. Phen uses the knowledge collected about a target including the frequency of changes and vulnerability history.
Phen will use system type, location proximity to the Internet where visibility of the system and increased opportunity to unauthorized access increases, services used (number of different services, increases the software on each system and increases the attack footprint increasing breach opportunities, looks into the usage of those services. One advantage is that if an adversary that wants to access the Enterprise, Phen constantly acquires additional information and provides security monitoring and defenses that are unique to each target throughout the system as a whole as well as its components.
Phen.AI can throttle the amount and depth of cyber-defense based on history and knowledge of your entire network. It can simultaneously focus on both the full network as well as smaller subsets, down to individual machines and devices. Phen also can rapidly ingest and analyze massive amounts of PCAP data, amounts that are too much for any human or team to understand in real-time, and will be able to capture and analyze vast amounts of the network traffic data.
CanSecure
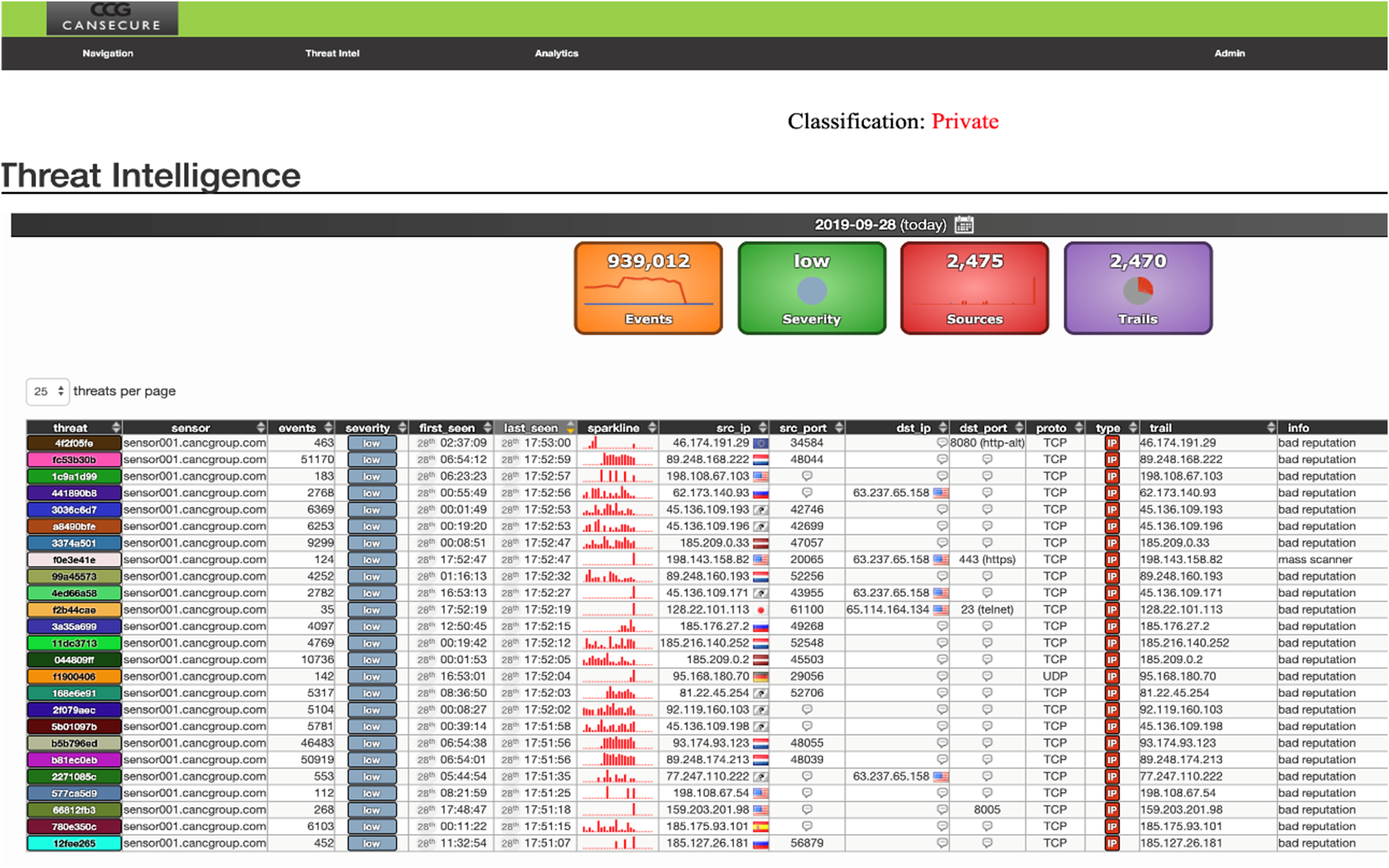
This solution contains patent-pending technology providing the ability to detect and manage known vulnerabilities as well as use fuzzing to detect anomalies and penetrate systems with new and unknown flaws. It uses well known suggested settings and configurations from NIST, DISA, and others to ensure systems are configured to be as secure as possible. CanSecure has an extensively written API allowing the integration of our signature vulnerability scanning software with third-party products. The CCG-designed humanoid artificial intelligence is used to perform system administrative duties involving configuration setup and adjustments, fault correction and extending system scanning, penetration testing, Red and Blue Team exercises capabilities of devices.
It provides auditing that follows various leading standards for compliance (NIST, PCI-DSS, CAESARS) and ensures configuration checks and settings comply with industry standards (NIST, DISA-STIG, SCAP). It uses standard risk assessment scoring (NIST CVSS) and reporting to help identify and prioritize the resolution of vulnerabilities..
NeTERS
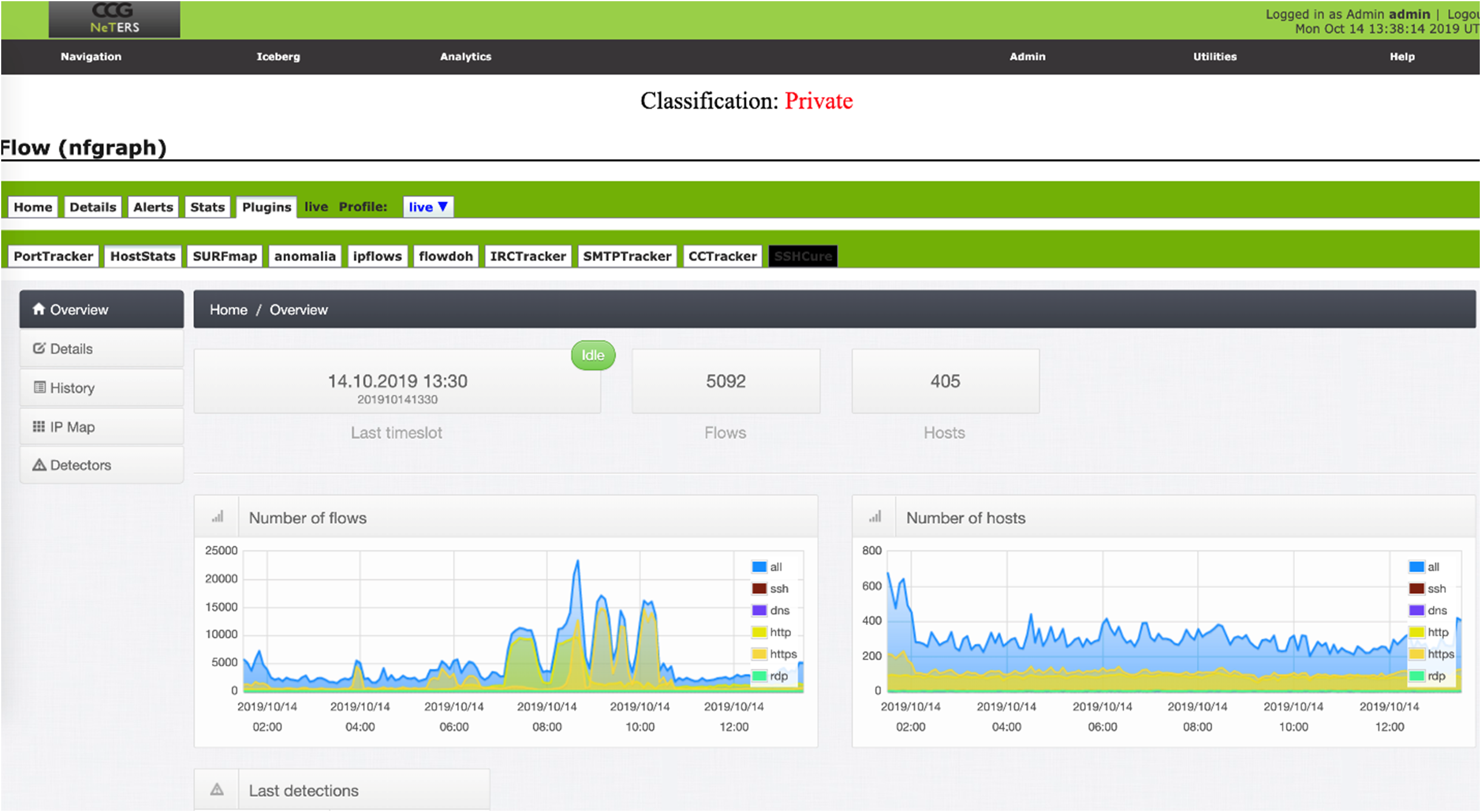
This solution provides a higher collection and view of the network’s activities, objects, and evolution, IE: ‘weather patterns.’ Providing system and application data paths throughout the customer’s network. Network traffic detects trends, hotspots, communication patterns, device interactions, importance of areas in the network.
We utilize a lighter level packet inspection vs a traditional IDS, to provide an array of low-cost sensors to enable seeing all activities and actions inside the network. NeTERS works in conjunction with existing IDSs or can provide those capabilities within NeTERS. Packet capture provides malware detection and flow through the network and between hosts, identifies files and watches how they are passed throughout the network, and detects data exfiltration.
NeTERS has the ability to tag, collect, trace and inspect media documents, file documents, web code, and applications in transit, and identifies where various files have moved through the network. NeTERS can also track viruses and virus paths, identifying which systems have been infected. NeTERS can also create network maps in real-time, and has the ability to correctly reconstruct the state of the network at any point in time.
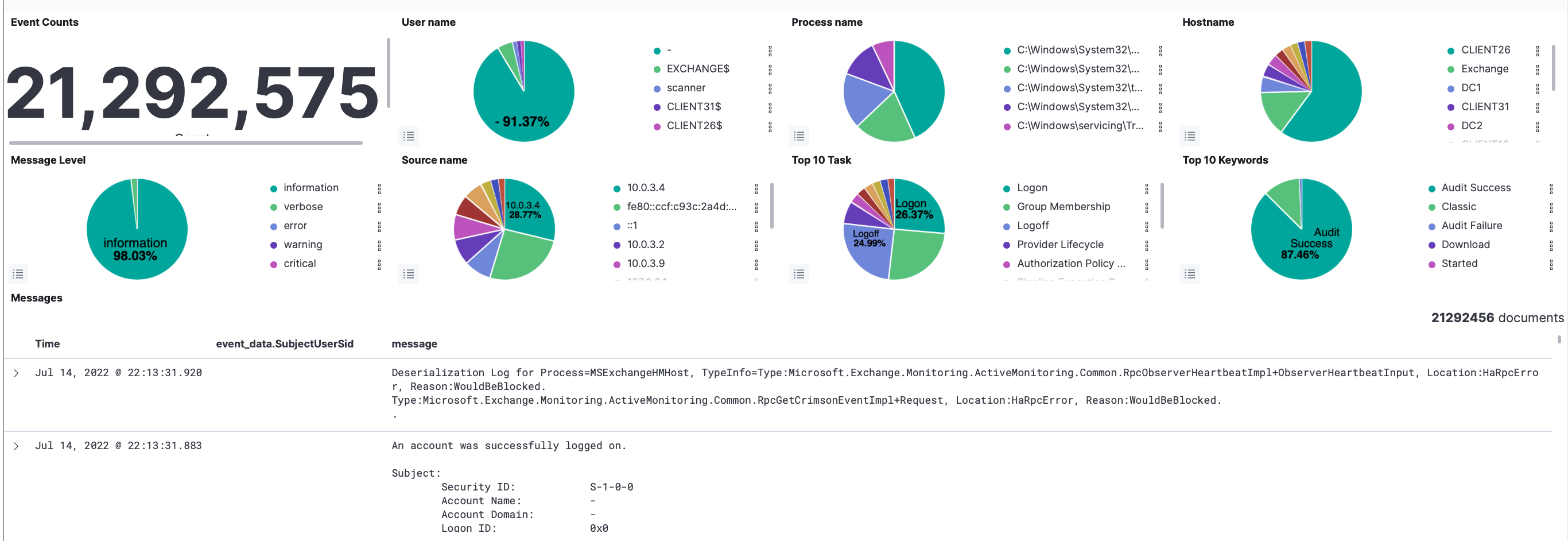
SLA, The SMART LogAnalyzer (SLA)
The SMART LogAnalyzer (SLA) will utilize an analytic and HDFS cloud storage systems for collection and processing of ingested information (EX: Netflow, device logs, alerts). Going to the cloud for storage allows continuous growth of log storage that will enable the software to process new cases in analysis for security purposes. Since cloud storage is built on commodity hardware, and expandable on-demand, it reduces the cost to start and grow your data set.
Since SLA provides a log repository from many different systems, it is able to make correlations between logs that were never before available. Providing full insight into users’ movement through the network and analysis of systems like never before. Since this contains the logs of your entire enterprise, including their weaknesses and attack points, you want to keep this in-house and have full control over the data. You don’t want to unwittingly expose your site by providing the keys to enter. SLA provides the security necessary to guard and protect these key information assets. Our threat analyzer (a component of SLA) provides a mechanism to explore and use business intelligence techniques to ferret out relationships among the data sets to further identify strengths, weaknesses, and vulnerabilities. SLA provides real-time monitoring, signature alerting, personal profiling, and anomalous activity detection, and provides a graphic interface that goes beyond simple graphic indexing with CCG-provided visuals and dashboards.