Enlists the power and security of CCG software data at your fingertips, anytime, anywhere.
The data and understanding of your environment are great. But it’s essential to obtain a full understanding when you are not at work. During an alert or heightened event, getting detailed, accurate information is critical.
CCG provides protection of all portable devices, including your phone.
This interface is available from any phone (or tablet) that has an internet connection and the ability to use a secure browser.
Getting Started
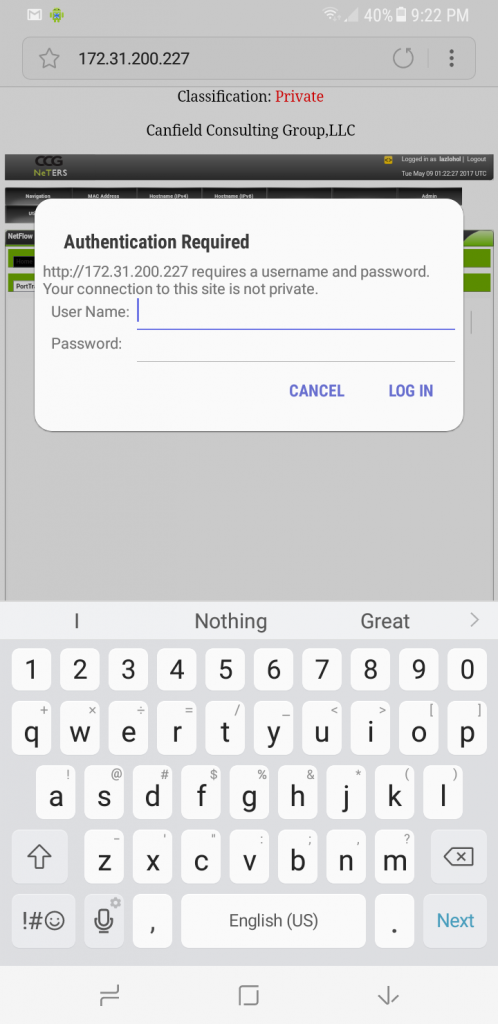
Logging in
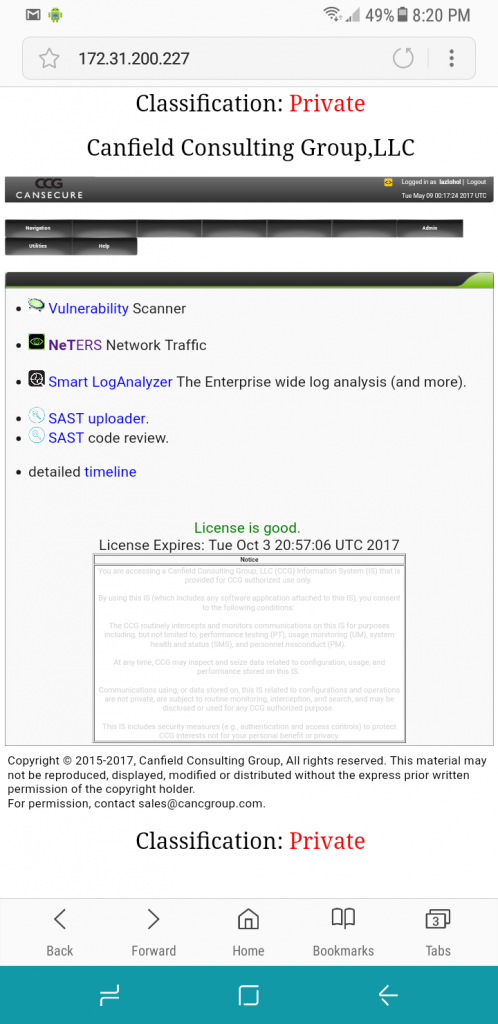
Home, quick access to the CCG installed software components
Interface into NeTERS:
NeTERS provides new algorithms to dig quickly and deeply into internal network traffic to provide accurate device detection and activities. NeTERS collects Netflow from a wide variety of sources: Cisco, PaloAlto, nProbe, softflowd, fprobe, etc. NeTERS distributes sensors to collect the entire internal traffic data, providing proprietary collection methods, industry-standard methods, and processing power to collect and deliver the data to the central system.

NeTERS internal Map, presents a realtime view of your network. Presenting microsecond detection and view of new devices and ports.
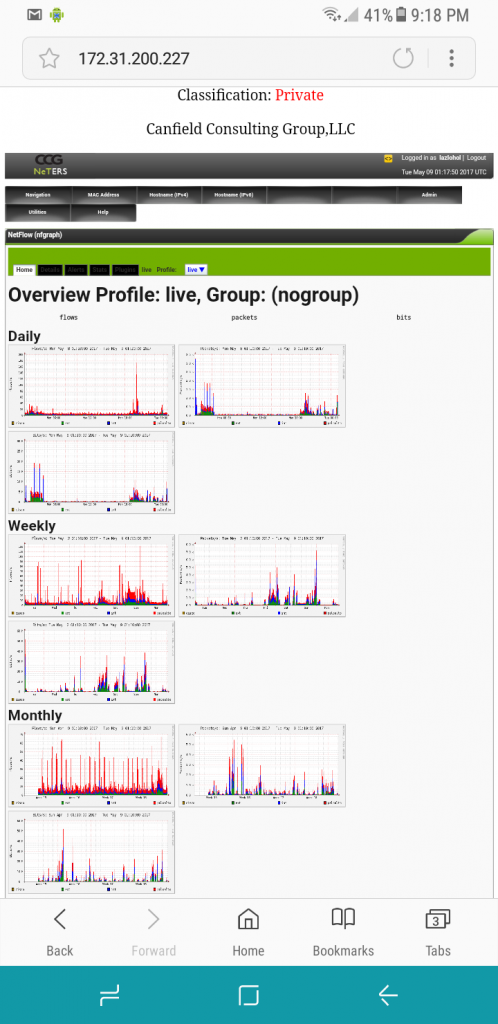
NetFlow Overview, providing daily, weekly, monthly, and yearly graphs of flows, packets and bytes
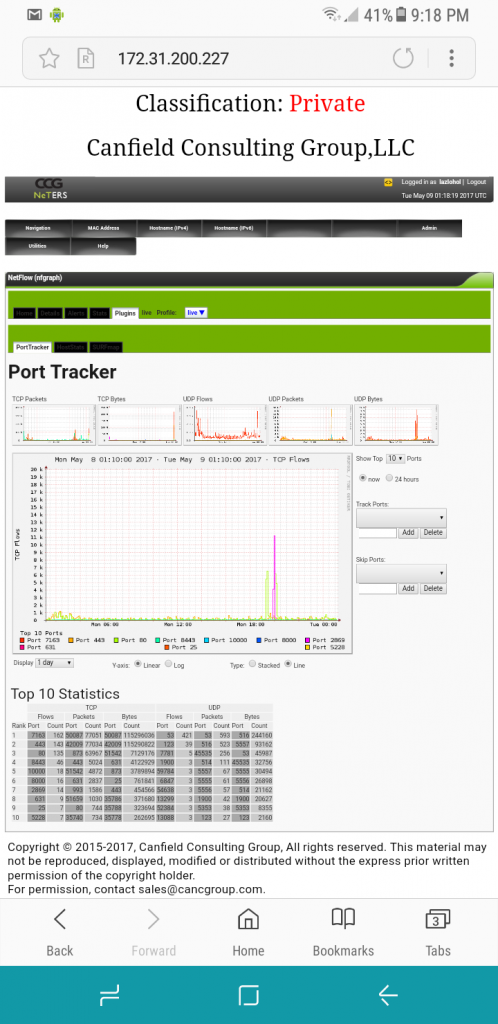
Port Analytic, allowing investigation and reporting on port usage
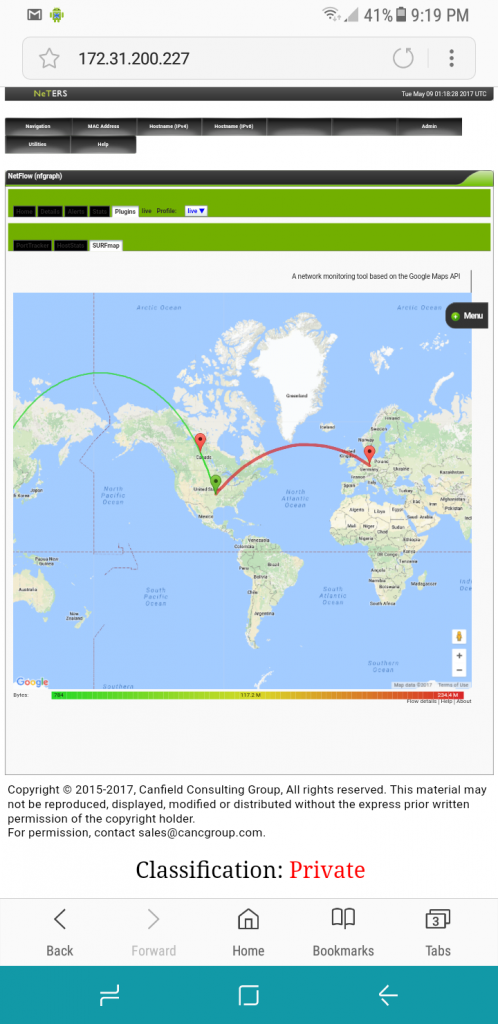
NetFlow World Map, this is the highest level view of world traffic events.
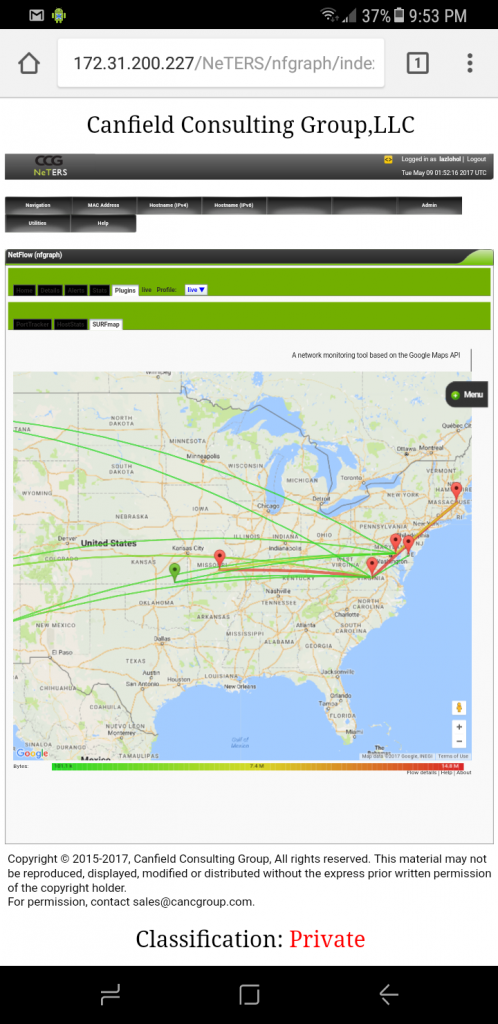
NetFlow Regional Map, this is the ‘regional’ view of traffic events.
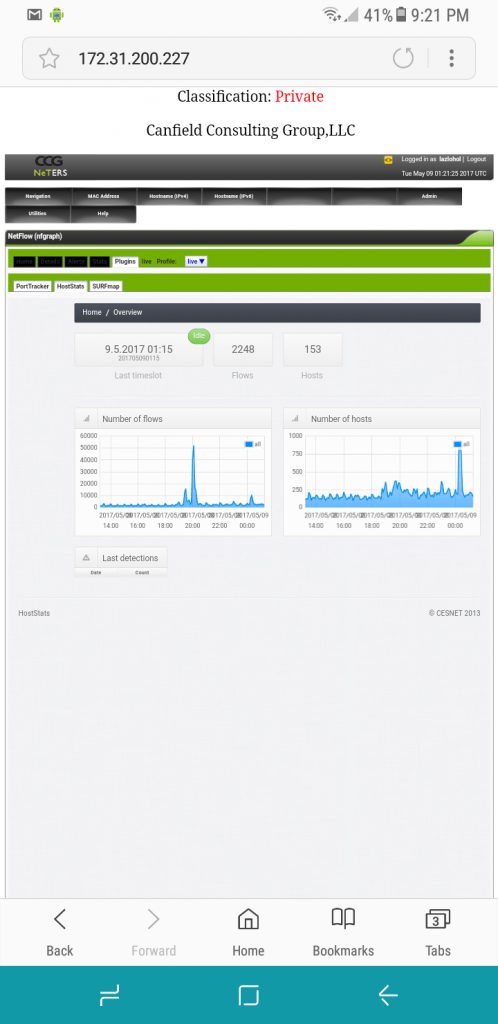
Hostinfo Analytic, investigate, analyze and report on host usage
Viewing the Smart LogAnalyzer (the SIEM):
The Smart LogAnalyzer (SLA) allows the central collection of data. This includes all collected NeTERS data sets, as well as Syslog, NtopNG, DNSensor, HTTP, and SMTP data sets. Included are Phen-provided analytics and analytic space to process and understand the actions of all components in your network and the network in its entirety.
SLA is the place to go for the security team when they wish to analyze and understand what’s happening inside the network.
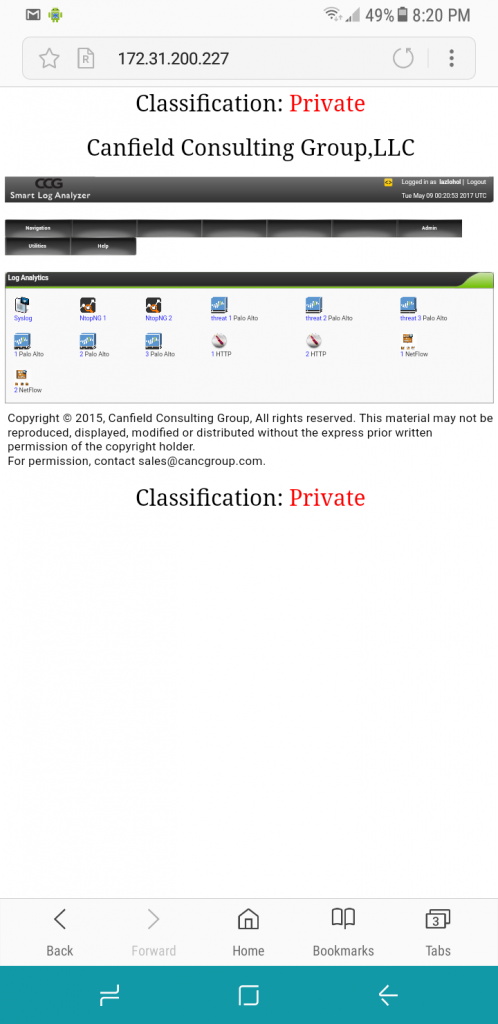
SIEM Reports index, index into the provided dashboards
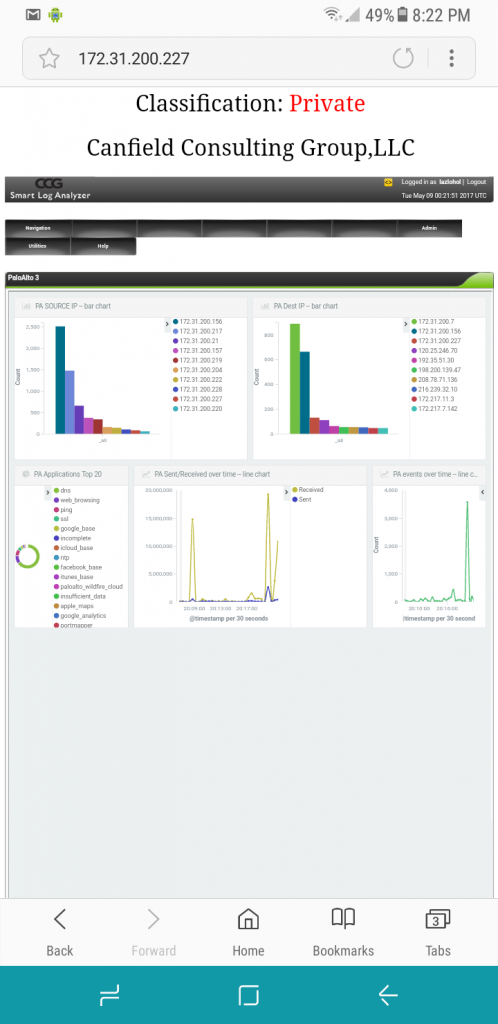
PaloAlto traffic, insight into the traffic data processed by the PaloAlto.
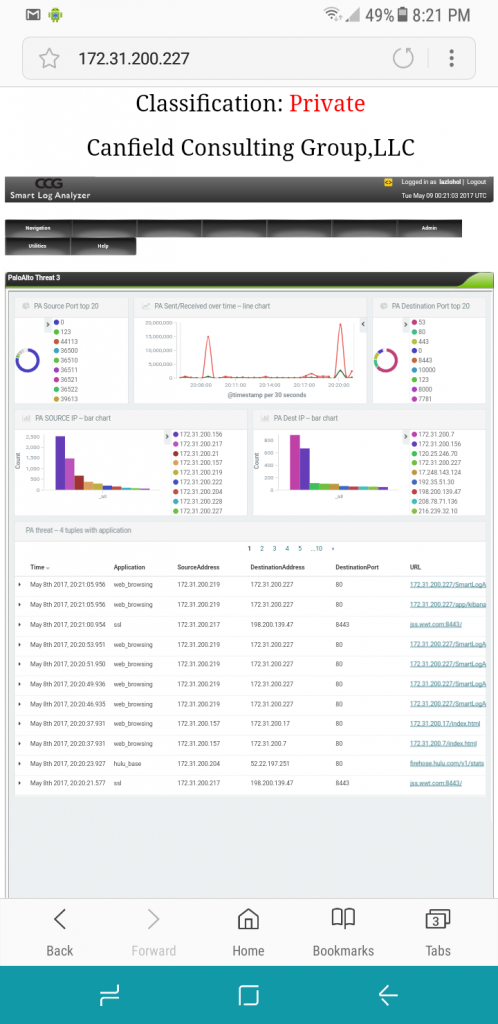
PaloAlto threats, organization, and structure of the PaloAlto created and/or reported threats.
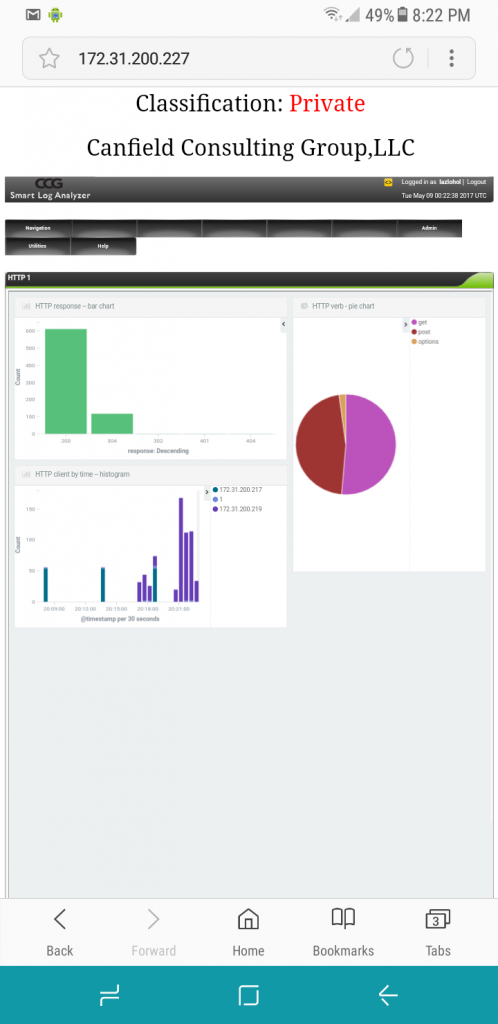
Web Traffic, the web traffic analyzer
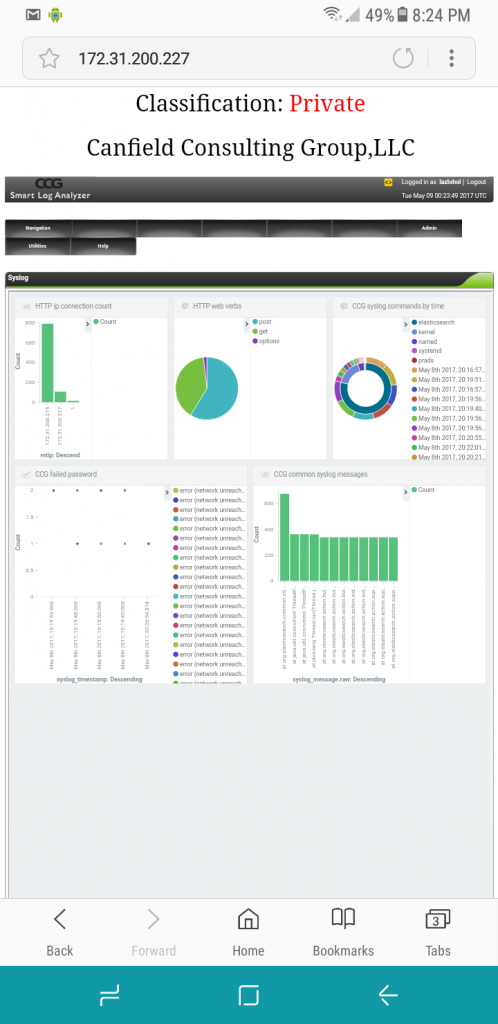
Syslog Activity, Syslog analyzer





